human mistakes
oversight
Massive Scale
Networks with millions of endpoints overwhelm manual management.
Catastrophic Downtime
A single outage can cost millions in losses.
Talent Shortage
Nearly 4 million unfilled cybersecurity jobs mean constant risks.
Legacy Systems
Older devices lack the power for complex crypto.
Resource Constraints
Limited memory and power budgets make PKI a drag.
Geographic Spread
Remote assets with spotty connections expose vulnerabilities.
- Manual renewals and revocations demand endless oversight.
- Centralized authorities create massive breach risks.
- Heavy asymmetric encryption taxes your systems.
- Retrofitting legacy tech is costly and disruptive.
- Human mistakes in handling certificates dominate breaches.
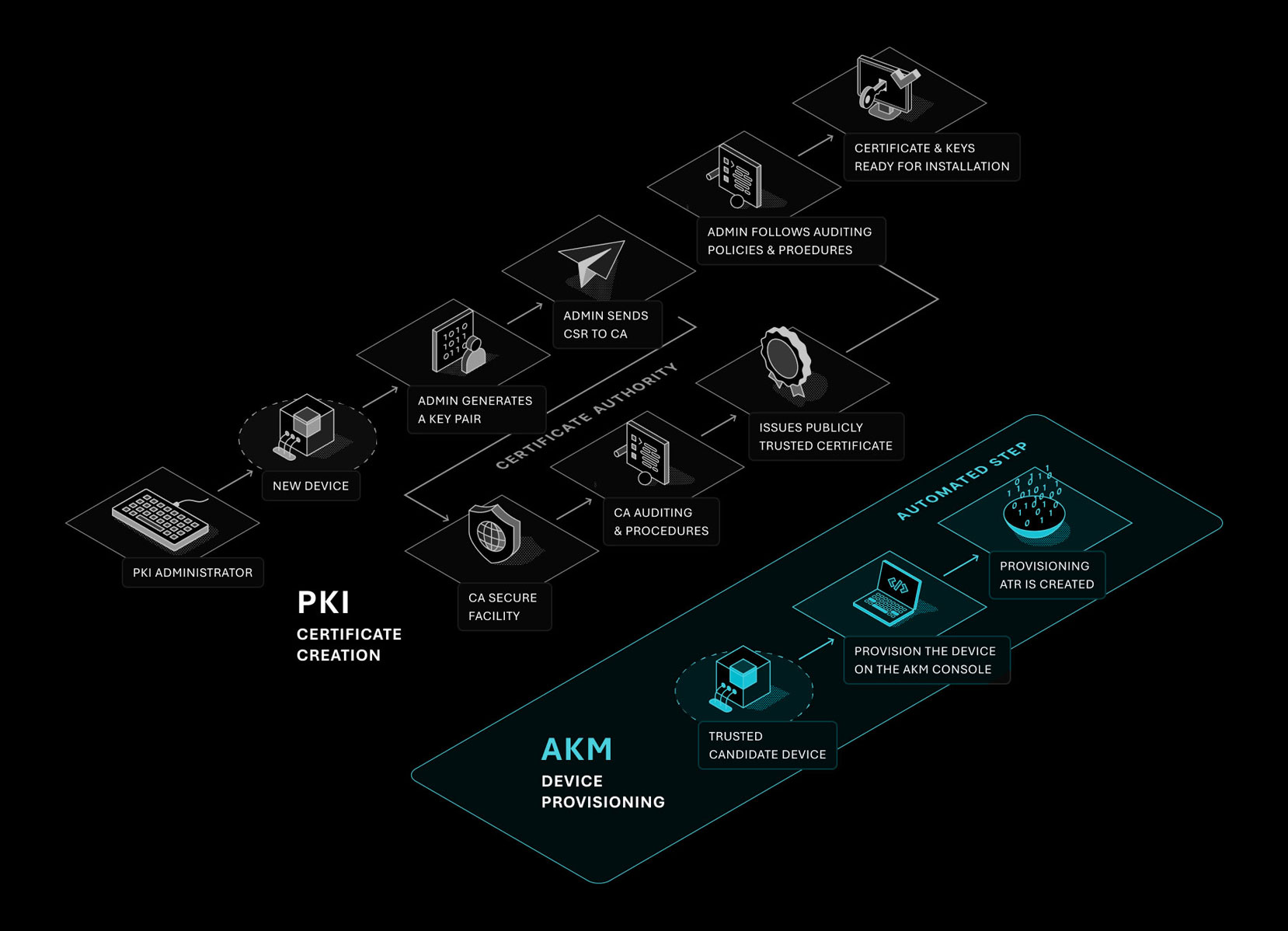
Many organizations limp along with outdated or no security at all. AKM changes that with an autonomous, lightweight, distributed, and self-healing alternative.
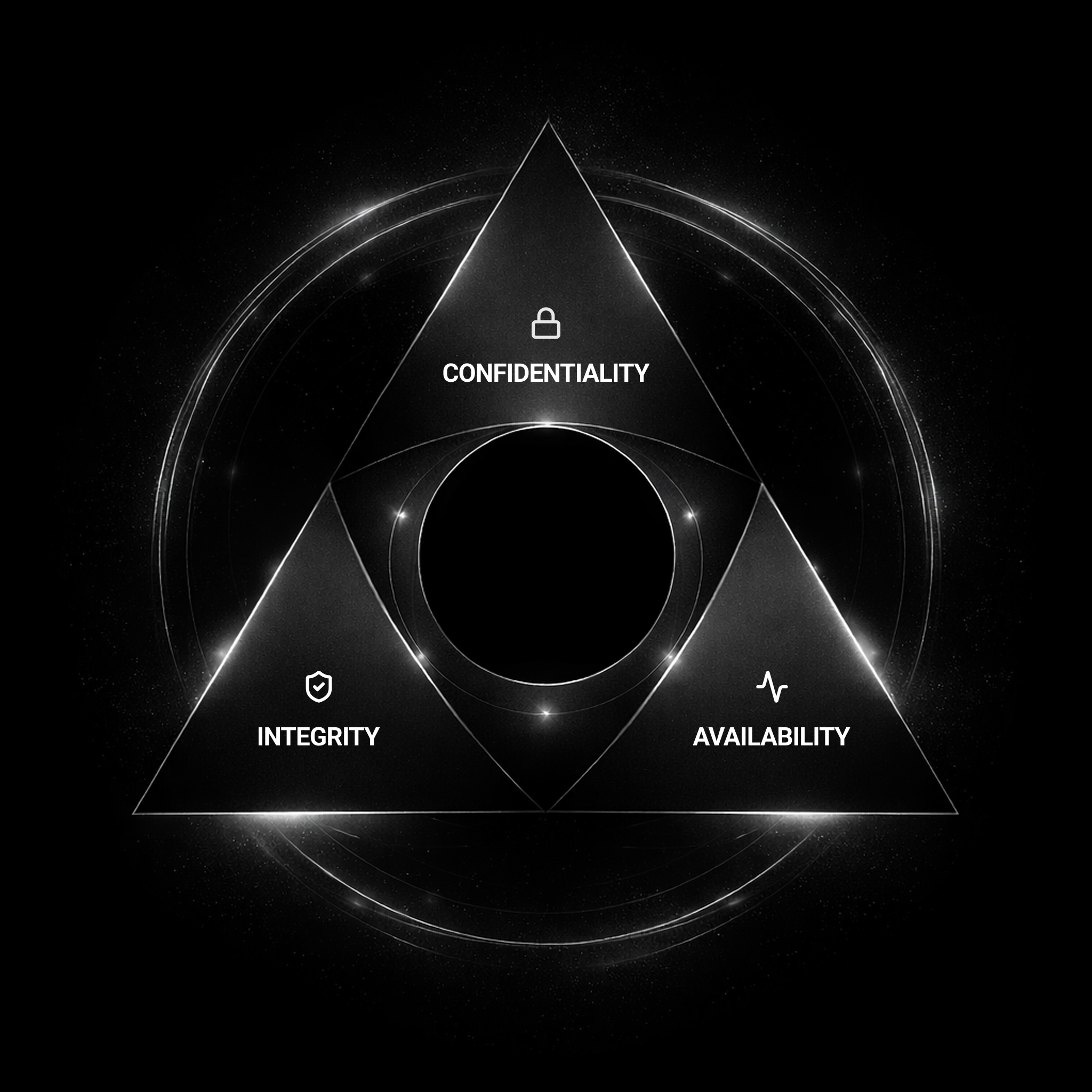
Confidentiality
Fresh, session-based keys keep data locked tight.
Integrity
Secret-free verification blocks spoofing and tampering.
Availability
Auto-fixes and quick recoveries keep you up and running.
Enterprise IT & Cloud
Seamless email encryption, VPNs, and multi-cloud auth without the drag.
Contact UsDefense & Government
Air-gapped, self-healing security for classified networks and drones.
Contact UsFinance & Healthcare
Quantum-safe transactions and patient data protection that meets strict regs.
Contact UsIoT & Beyond
Lightweight keys for billions of devices, from smart homes to global supply chains.
Contact Us